2022HITCON
HITCON
密码学考试前夕的一场热身赛,RE只有三道题目,难度适中。虽然最后被打烂了,但AK的快感还是慰藉人心的。
密码学考后整理的wp,顺便把题目记录在此,以便今后CUMT的学弟学妹们参考~
2020CUMT-Crypto
基本不考察理论背诵和算法记忆(除了AES、DES、SM4)
第一大题(30分)
- 画出Feistel一轮的流程图
- 给定消息bit数问hash(MD5)的填充方式
- 给定6位密码包括0-9和a-z分析秘钥空间
- 给定一串字符计算游程的个数(要首尾连接)
- aes的子密钥多少bit,简述生成过程
- 给6bit值计算des的sbox替换
第二大题(30分)
- 给定仿射加密式求解密,本次解密结果为CUMT
- AES列混淆中GF(2^8)域上的乘法,多项式运算,本年计算0x2*0xc1
- RSA给定p、q、e小数据,要求解密密文
第三大题(20)
- 证明DES有代数互补性、画出CBC的解密图
- LFSR给定一个特征多项式,要求画出LFSR的图和给出f函数,第二问是给定初始状态求输出序列和周期
第四大题(20)
一大题,三小问,本年度考察EIGAMAL算法,公钥只要求记忆RSA的算法,所以EIGAMAL和ECC的算法都会给出。
- EIGAMAL的公钥和私钥(5)
- 证明算法的正确性(5)
- 给定参数实现加密和解密(10)
REVERSE
Checker
checker程序主要就是使用DeviceIoControl函数向驱动程序发送控制码。
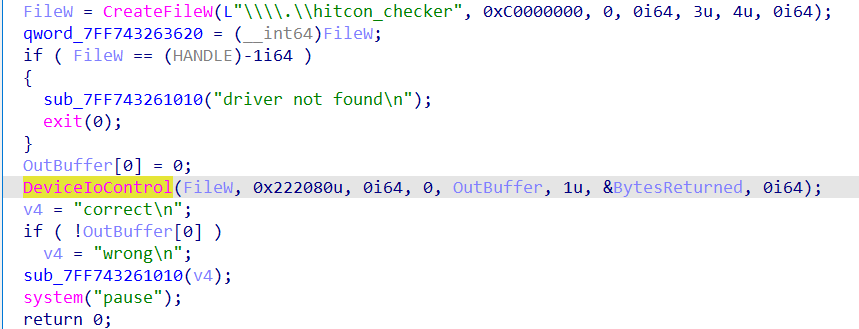
驱动程序中还包括其他的控制码并进行运算,并控制了一个bool数组,当bool数组全为1时check通过,所以出题人是要我们向驱动程序按某种顺序传入控制码,满足条件后运行checker即输出correct。
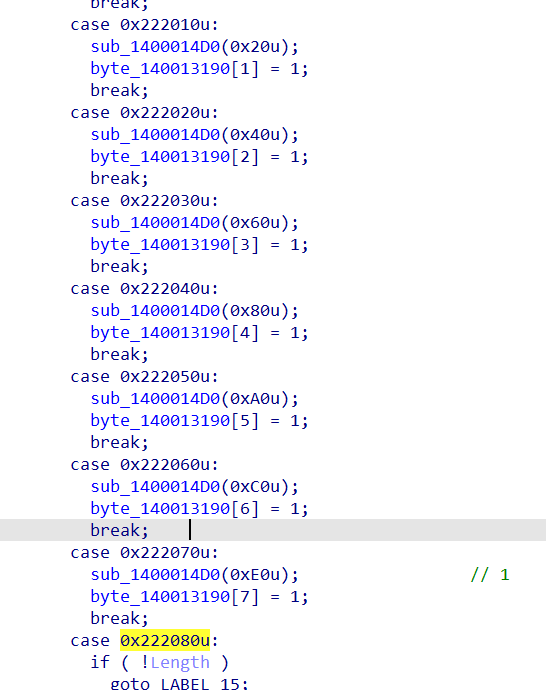
在驱动初始化时使用了一些重定位来隐藏真正访问的变量,通过计算恢复各个偏移指向的虚拟地址。
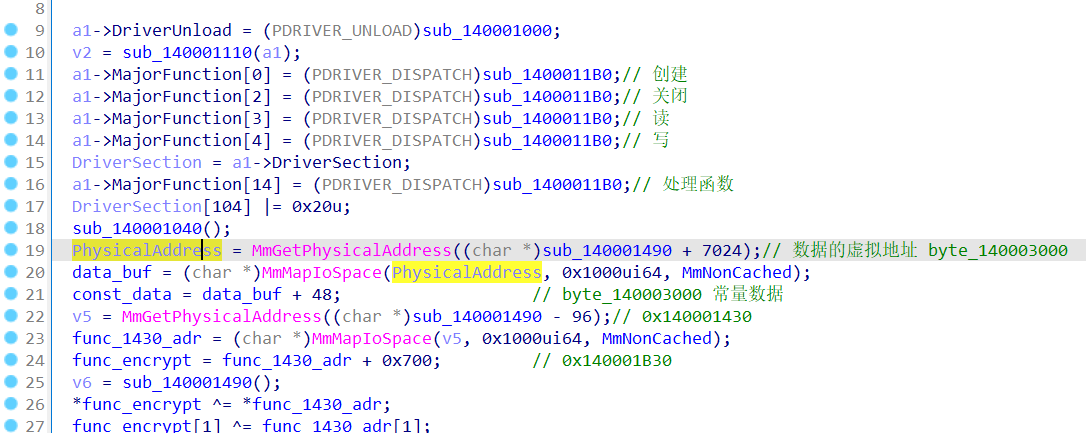
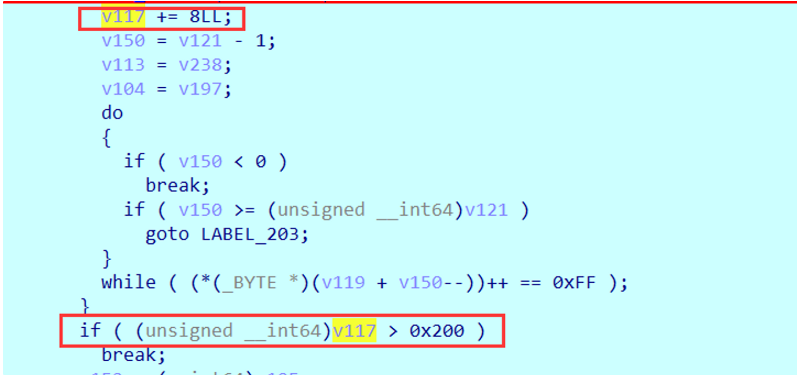
func_encrypt指向的是0x140001B30 地址,并且每次进入sub_1400014D0函数后,都会在调用前进行对其进行异或和调用后异或,异或的常量通过传入的参数来找偏移。
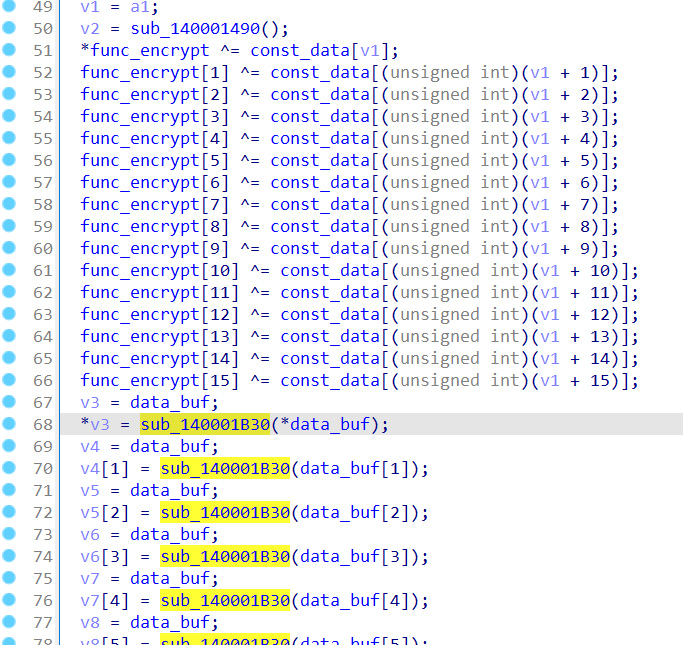
所以之后就要确定正确的调用顺序,这里观察到对data_buf数据的处理是单字节,且存在ecx中,可以观察异或后sub_140001B30函数的汇编来确认异或顺序,这里我使用capstone手撸的
exp
1 | |
meow_way
通过交叉引用可知,使用 initterm函数将全局变量与函数绑定。

访问函数题可见经典的32位程序调用64位代码的格式,代码比较短也用capstone。
1 | |
=.=用了最麻烦的方法手撸
1 | |
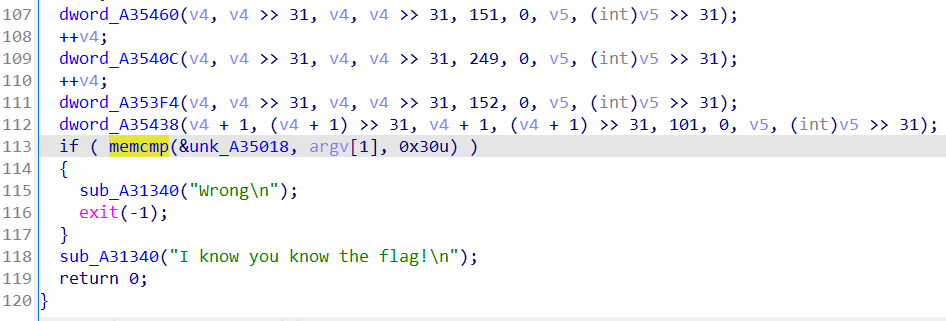
因为他是单字节加密,patch一个printf,使用subprocess爆破也可以。
😭 gocrygo
go的恶意软件修复题,加密为3DES加密一个随机数据作为秘钥流,搜寻秘钥可以结合被加密文件首部的8字节随机数在core中搜索。因为是流密码,所以找到3DES秘钥扩展后的秘钥patch进去调试即可解密。
1 | |
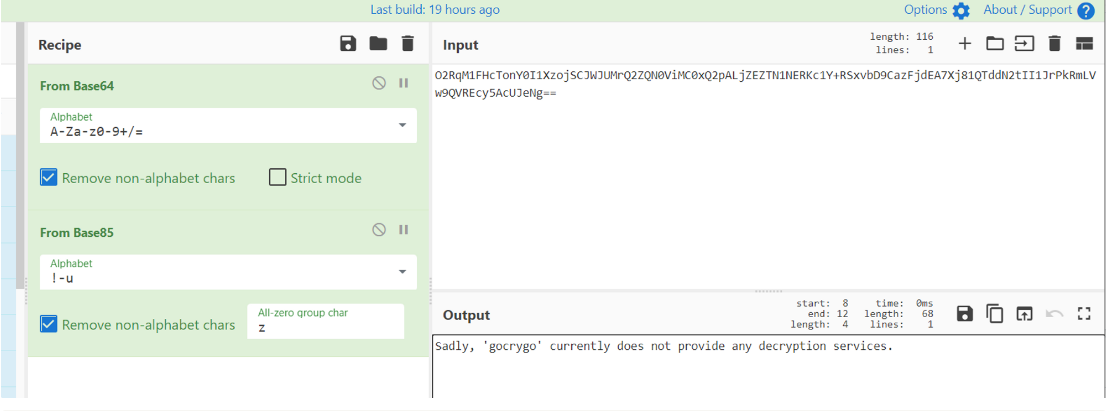
内存中的一些base64解密后再base85可见明文,关于题目的提示信息。
1 | |
L29iaw==解密后是.qq也就是加密文件新后缀,sub_2214EB是负责解密数据的函数,这样大概能调了,.gocrygo表示已经加密过,调试的时候注意删除。
sub_2126AE 函数是DES的秘钥扩展,使用了3次,3DES可能,key是生成的24字节随机数。
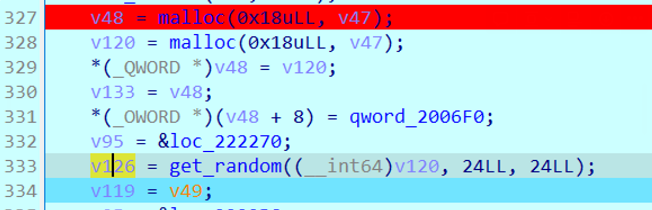
3DES的加密,sub_2123D为其feistel结构,用3DES加密获取的8字节rand2。
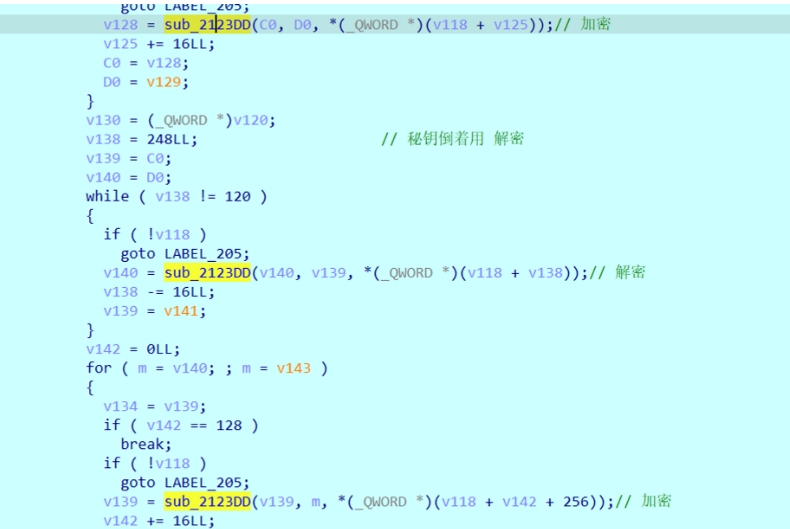
1 | |
之后会将rand2+1,然后继续使用3DES加密,直到生成0x200bit的密文,把生成的密文和文件的明文逐字节异或得到解密后的文件,会将初始的rand2写在被加密文件的前8字节。
1 | |
rand2被写在文件前8字节,所以主要就是找rand1的24个字节了,针对flag.txt加密的。
1 | |
突然发现变换后的rand2 和 最后异或的流秘钥在内存中十分接近,也就是直接在转储中搜58 7E 75 76 AA 07 F4 41 !!!
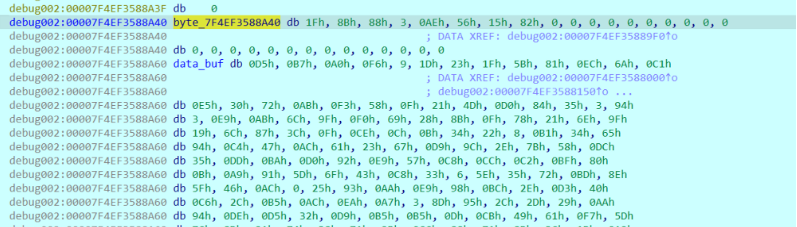
搜索被加密文件首部八字节定位存储的轮秘钥。
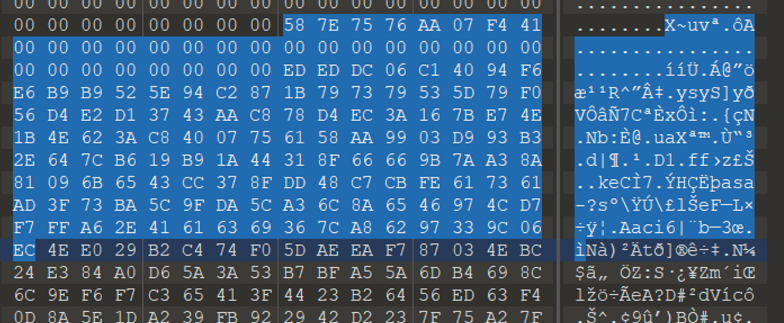
1 | |
这仅能解密直接小于512的文件,因为存储的流秘钥512字节一组并不断更新。
发现文件路径和rand2之间的3DES扩展秘钥等比较容易定位,在dump出的内存中搜索首部8字节,并dump其上的768字节在3DES生成扩展秘钥后patch。
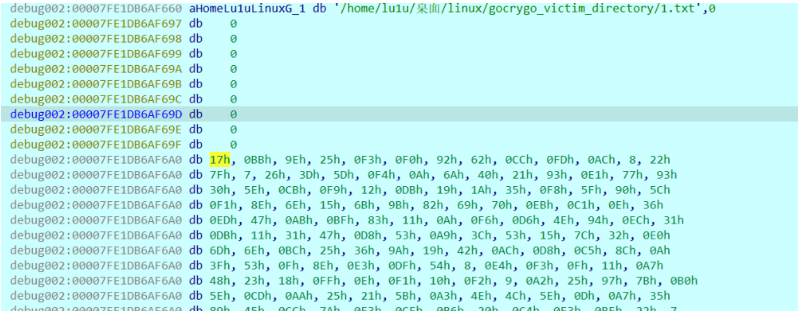
调试即可完成解密,和以往恶意软件常用的RC4、Sasal20类似,3DES的OFB模式生成的轮秘钥
在core里面找patch数据直接搜加密文件的前8字节,前面有768字节并且会有路径的字符串。
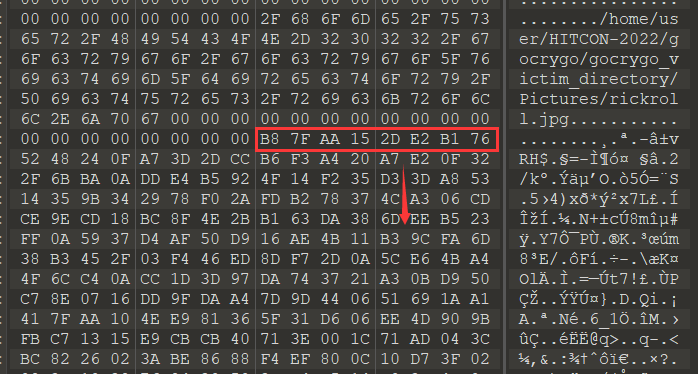
1 | |
对称密码真就是逆向手的自我修养~
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!