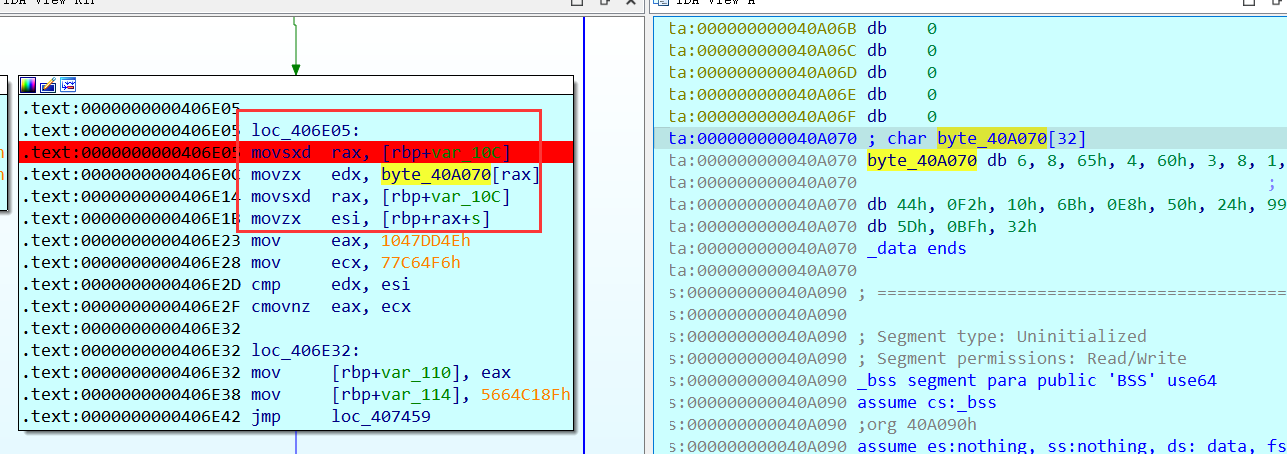
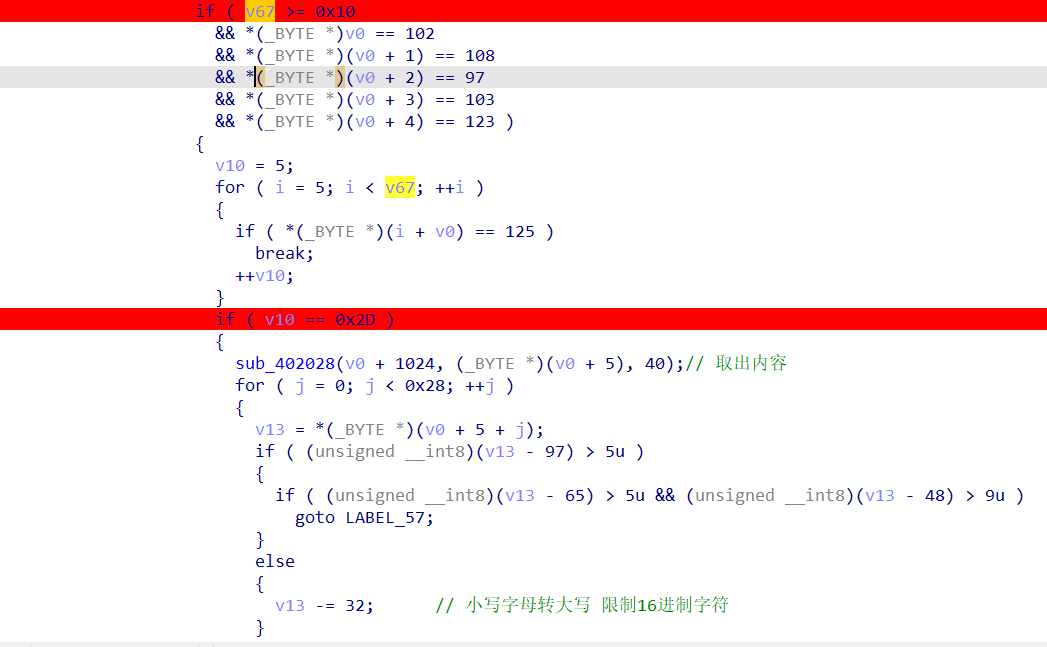
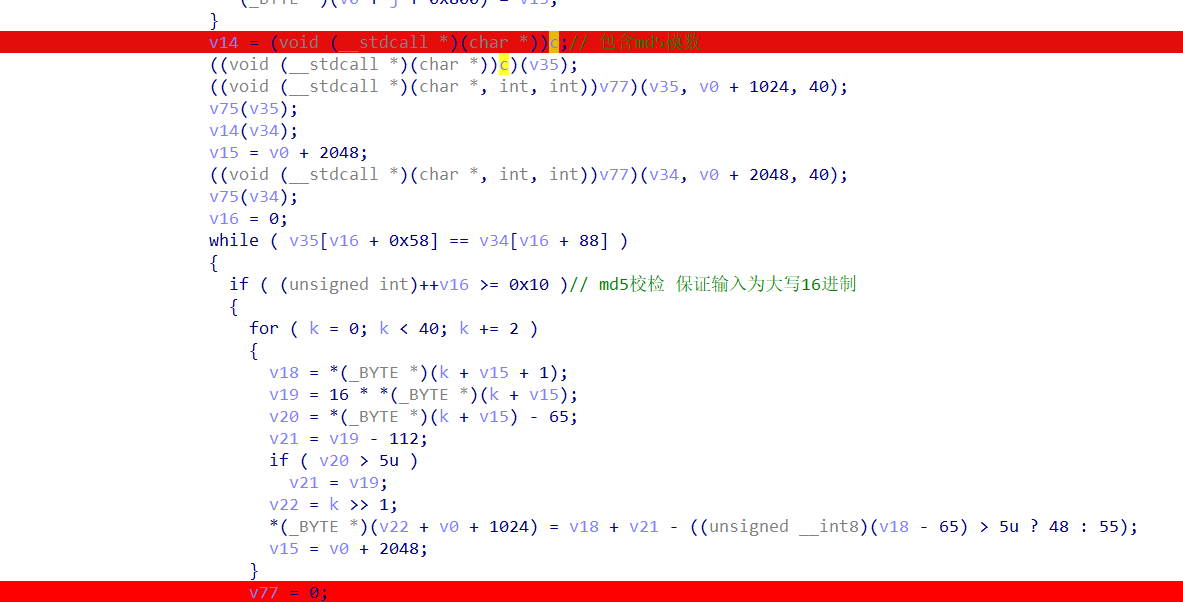
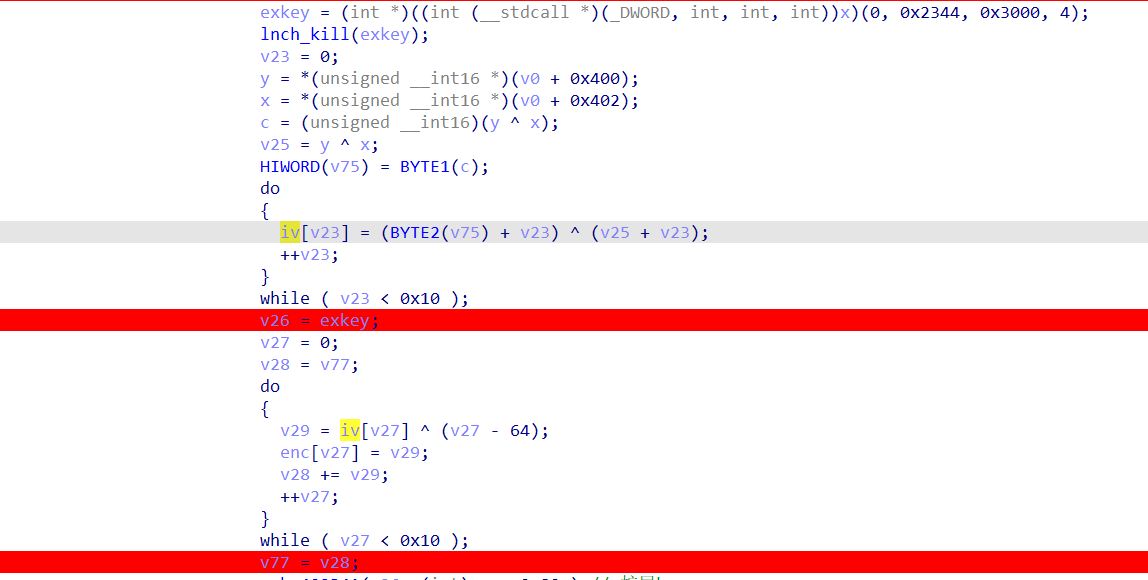
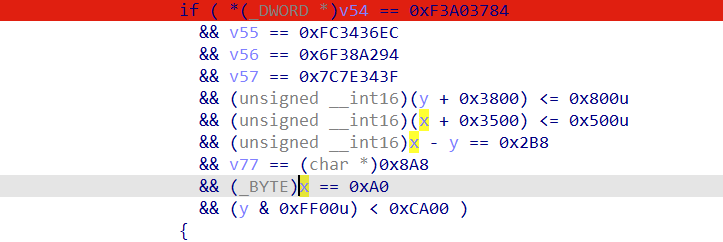
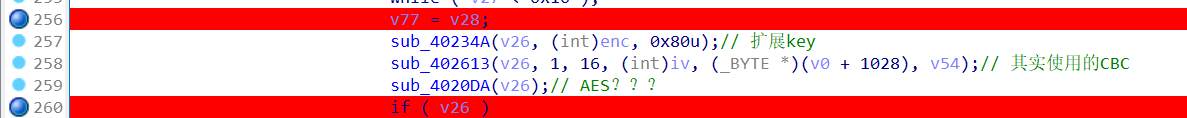
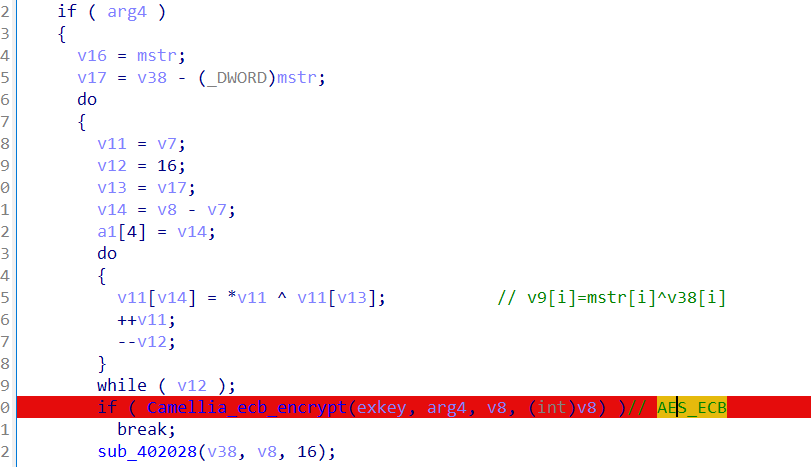
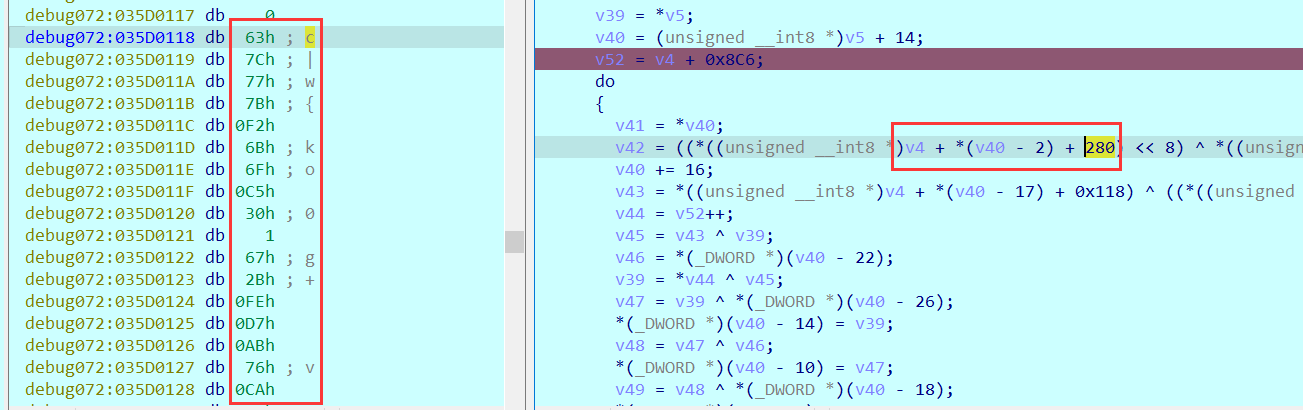
1
2
3
4
5
6
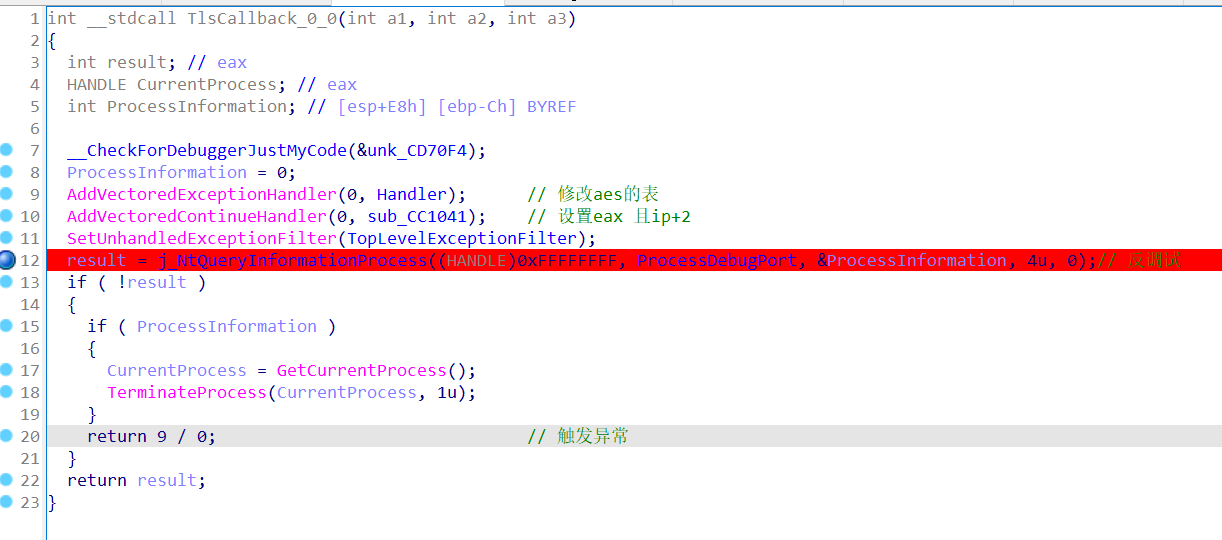
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
| def hexdump(s):
for i in range(len(s)):
print(hex(s[i])[2:].zfill(2),end=' ')
print()
def get_invs(sb:list):
out=[0]*256
for i in range(256):
out[sb[i]]=i
return out
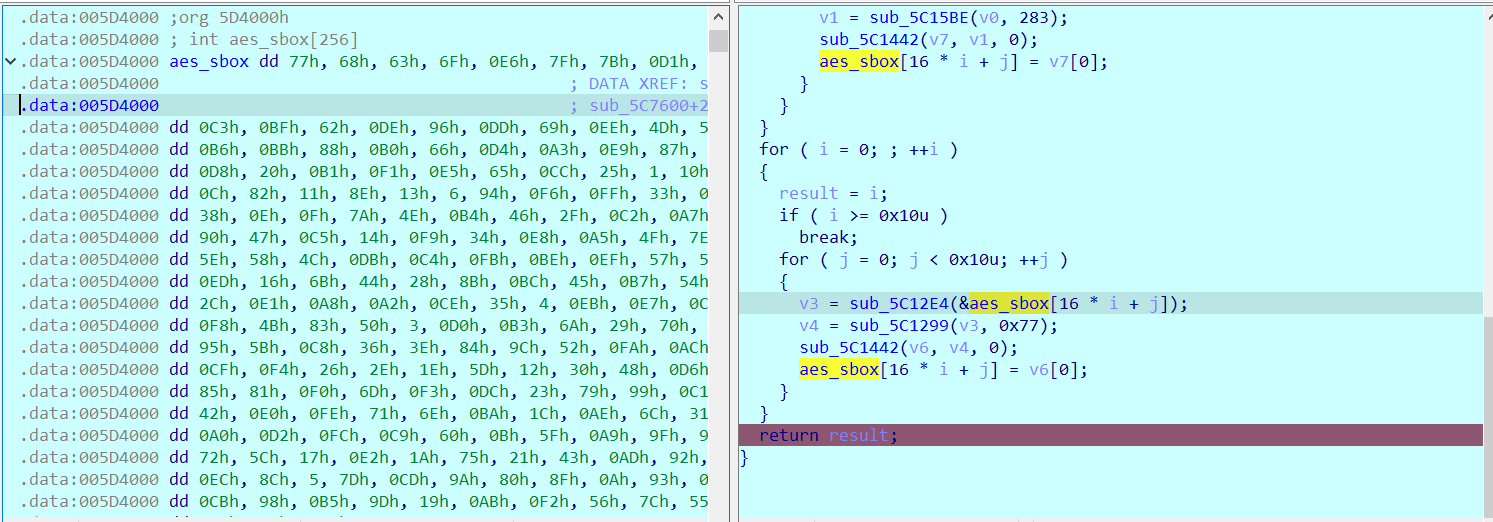
sbox=[0x00000077, 0x00000068, 0x00000063, 0x0000006F, 0x000000E6, 0x0000007F, 0x0000007B, 0x000000D1, 0x00000024, 0x00000015, 0x00000073, 0x0000003F, 0x000000EA, 0x000000C3, 0x000000BF, 0x00000062, 0x000000DE, 0x00000096, 0x000000DD, 0x00000069, 0x000000EE, 0x0000004D, 0x00000053, 0x000000E4, 0x000000B9, 0x000000C0, 0x000000B6, 0x000000BB, 0x00000088, 0x000000B0, 0x00000066, 0x000000D4, 0x000000A3, 0x000000E9, 0x00000087, 0x00000032, 0x00000022, 0x0000002B, 0x000000E3, 0x000000D8, 0x00000020, 0x000000B1, 0x000000F1, 0x000000E5, 0x00000065, 0x000000CC, 0x00000025, 0x00000001, 0x00000010, 0x000000D3, 0x00000037, 0x000000D7, 0x0000000C, 0x00000082, 0x00000011, 0x0000008E, 0x00000013, 0x00000006, 0x00000094, 0x000000F6, 0x000000FF, 0x00000033, 0x000000A6, 0x00000061, 0x0000001D, 0x00000097, 0x00000038, 0x0000000E, 0x0000000F, 0x0000007A, 0x0000004E, 0x000000B4, 0x00000046, 0x0000002F, 0x000000C2, 0x000000A7, 0x0000003D, 0x000000F7, 0x0000003B, 0x00000090, 0x00000047, 0x000000C5, 0x00000014, 0x000000F9, 0x00000034, 0x000000E8, 0x000000A5, 0x0000004F, 0x0000007E, 0x000000DF, 0x000000AA, 0x0000002D, 0x0000005E, 0x00000058, 0x0000004C, 0x000000DB, 0x000000C4, 0x000000FB, 0x000000BE, 0x000000EF, 0x00000057, 0x00000059, 0x00000027, 0x00000091, 0x00000051, 0x000000ED, 0x00000016, 0x0000006B, 0x00000044, 0x00000028, 0x0000008B, 0x000000BC, 0x00000045, 0x000000B7, 0x00000054, 0x0000009B, 0x00000086, 0x00000089, 0x0000002C, 0x000000E1, 0x000000A8, 0x000000A2, 0x000000CE, 0x00000035, 0x00000004, 0x000000EB, 0x000000E7, 0x000000C6, 0x000000D9, 0x00000018, 0x00000007, 0x000000F8, 0x0000004B, 0x00000083, 0x00000050, 0x00000003, 0x000000D0, 0x000000B3, 0x0000006A, 0x00000029, 0x00000070, 0x00000049, 0x0000000D, 0x00000067, 0x00000074, 0x00000095, 0x0000005B, 0x000000C8, 0x00000036, 0x0000003E, 0x00000084, 0x0000009C, 0x00000052, 0x000000FA, 0x000000AC, 0x00000000, 0x000000CA, 0x0000004A, 0x0000001F, 0x000000CF, 0x000000F4, 0x00000026, 0x0000002E, 0x0000001E, 0x0000005D, 0x00000012, 0x00000030, 0x00000048, 0x000000D6, 0x000000C7, 0x000000B8, 0x00000076, 0x00000085, 0x00000081, 0x000000F0, 0x0000006D, 0x000000F3, 0x000000DC, 0x00000023, 0x00000079, 0x00000099, 0x000000C1, 0x0000005A, 0x000000BD, 0x00000078, 0x00000042, 0x000000E0, 0x000000FE, 0x00000071, 0x0000006E, 0x000000BA, 0x0000001C, 0x000000AE, 0x0000006C, 0x00000031, 0x0000003A, 0x00000008, 0x000000B2, 0x000000A0, 0x000000D2, 0x000000FC, 0x000000C9, 0x00000060, 0x0000000B, 0x0000005F, 0x000000A9, 0x0000009F, 0x0000009E, 0x00000064, 0x0000002A, 0x000000A1, 0x00000072, 0x0000005C, 0x00000017, 0x000000E2, 0x0000001A, 0x00000075, 0x00000021, 0x00000043, 0x000000AD, 0x00000092, 0x000000D5, 0x00000009, 0x0000008A, 0x000000F5, 0x000000EC, 0x0000008C, 0x00000005, 0x0000007D, 0x000000CD, 0x0000009A, 0x00000080, 0x0000008F, 0x0000000A, 0x00000093, 0x000000FD, 0x000000DA, 0x00000041, 0x0000003C, 0x000000CB, 0x00000098, 0x000000B5, 0x0000009D, 0x00000019, 0x000000AB, 0x000000F2, 0x00000056, 0x0000007C, 0x00000055, 0x0000008D, 0x00000039, 0x0000001B, 0x000000A4, 0x00000040, 0x000000AF, 0x00000002]
invsbox = get_invs(sbox)
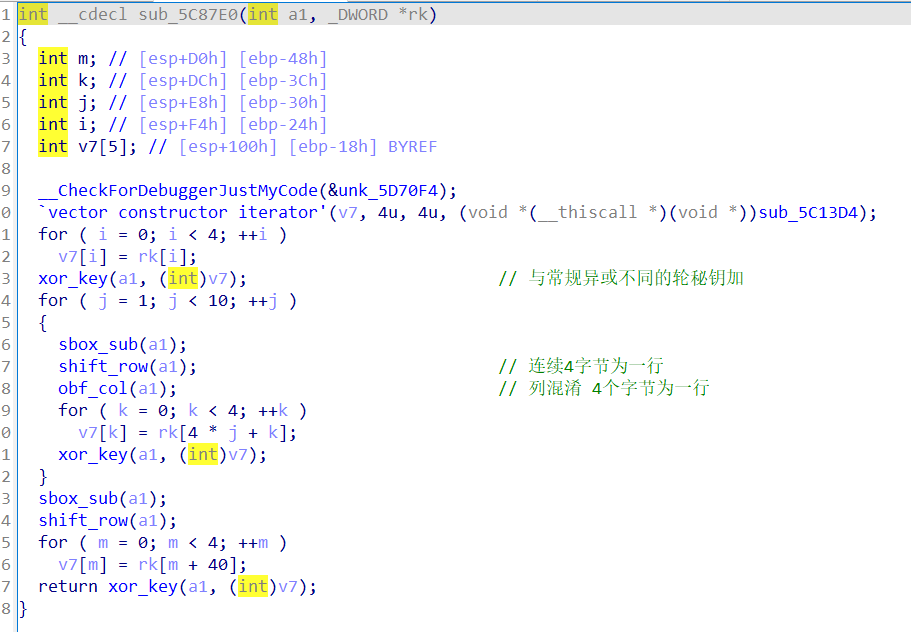
def round_key(m:list,rk:list):
for i in range(4):
for j in range(4):
m[4 * i + j] ^= rk[(3 - i) + 4 * j]
def inv_sub(m:list):
for i in range(len(m)):
m[i]=invsbox[m[i]]
def byte_sub(m:list):
for i in range(len(m)):
m[i]=sbox[m[i]]
def shift_row(s:list):
out=s[:4]
out.extend(s[5:8])
out.append(s[4])
out.extend(s[10:12])
out.extend(s[8:10])
out.append(s[15])
out.extend(s[12:15])
return out
def inv_shift_row(s:list):
out=s[:4]
out.append(s[7])
out.extend(s[4:7])
out.extend(s[10:12])
out.extend(s[8:10])
out.extend(s[13:16])
out.append(s[12])
return out
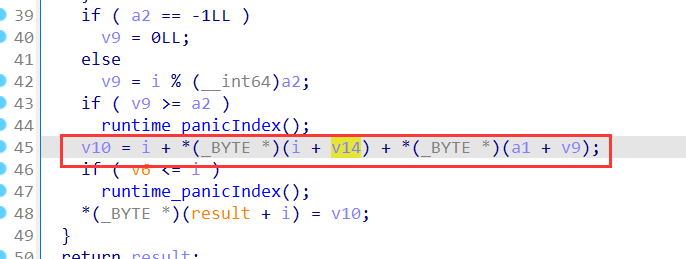
xtime = lambda a: (((a << 1) ^ 0x1B) & 0xFF) if (a & 0x80) else (a << 1)
def mix_single_column(a):
t = a[0] ^ a[1] ^ a[2] ^ a[3]
u = a[0]
a[0] ^= t ^ xtime(a[0] ^ a[1])
a[1] ^= t ^ xtime(a[1] ^ a[2])
a[2] ^= t ^ xtime(a[2] ^ a[3])
a[3] ^= t ^ xtime(a[3] ^ u)
def mix_column(c:list):
a = []
for i in range(4):
tmp = []
for j in range(4):
tmp.append(c[4 * j + i])
a.append(tmp)
for i in range(4):
mix_single_column(a[i])
cc = [0] * 16
for i in range(4):
for j in range(4):
cc[4 * j + i] = a[i][j]
return cc
def GFMul(a:int,b:int):
sig=0
ans=0
while a:
if(a&1): ans^=b
a>>=1
if a:
sig=(b>>7)&1
b=(b<<1)&0xff
if(sig) :b^=0x1b
return ans
def inv_mix_col(c:list):
tmp=[]
for i in range(4):
for j in range(4):
tmp.append(c[4*j+i])
m=[0]*16
for i in range(0,16,4):
m[i] = GFMul(0xe, tmp[i]) ^ GFMul(0xb, tmp[i + 1]) ^ GFMul(0xd, tmp[i + 2]) ^ GFMul(0x9, tmp[i + 3]);
m[i + 1] = GFMul(0x9, tmp[i]) ^ GFMul(0xe, tmp[i + 1]) ^ GFMul(0xb, tmp[i + 2]) ^ GFMul(0xd, tmp[i + 3]);
m[i + 2] = GFMul(0xd, tmp[i]) ^ GFMul(0x9, tmp[i + 1]) ^ GFMul(0xe, tmp[i + 2]) ^ GFMul(0xb, tmp[i + 3]);
m[i + 3] = GFMul(0xb, tmp[i]) ^ GFMul(0xd, tmp[i + 1]) ^ GFMul(0x9, tmp[i + 2]) ^ GFMul(0xe, tmp[i + 3]);
for i in range(4):
for j in range(4):
tmp[4*i+j]=m[i+4*j]
return tmp
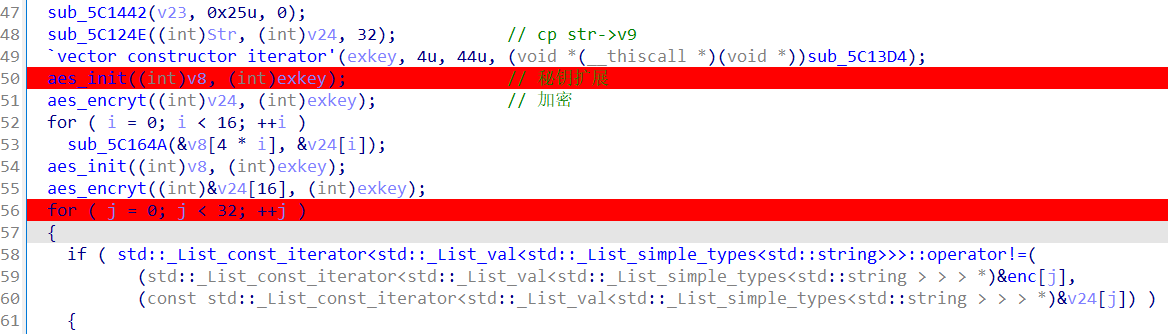
def encry(t:list,exkey:list):
m=t[:]
round_key(m,exkey[:16])
for i in range(1,10):
byte_sub(m)
m=shift_row(m)
m=mix_column(m)
round_key(m,exkey[16*i:16*i+16])
byte_sub(m)
m=shift_row(m)
round_key(m,exkey[160:176])
return m[:]
def decry(t:list,exkey:list):
c=t[:]
round_key(c,exkey[160:176])
c=inv_shift_row(c)
inv_sub(c)
for i in range(9,0,-1):
round_key(c, exkey[16 * i:16 * i + 16])
c=inv_mix_col(c)
c=inv_shift_row(c)
inv_sub(c)
round_key(c,exkey[:16])
hexdump(c)
return c
print('--- encry ---')
rk=[0x0C, 0x38, 0x93, 0x17, 0x54, 0xF7, 0xA7, 0x11, 0x20, 0xC8, 0x89, 0xF7, 0x25, 0xFA, 0x1A, 0xD4, 0x44, 0x07, 0xBE, 0xB4, 0x10, 0xF0, 0x19, 0xA5, 0x30, 0x38, 0x90, 0x52, 0x15, 0xC2, 0x8A, 0x86, 0x00, 0x5E, 0x9B, 0xC8, 0x10, 0xAE, 0x82, 0x6D, 0x20, 0x96, 0x12, 0x3F, 0x35, 0x54, 0x98, 0xB9, 0x56, 0xC8, 0xBB, 0x8A, 0x46, 0x66, 0x39, 0xE7, 0x66, 0xF0, 0x2B, 0xD8, 0x53, 0xA4, 0xB3, 0x61, 0xB9, 0x25, 0xF2, 0xEF, 0xFF, 0x43, 0xCB, 0x08, 0x99, 0xB3, 0xE0, 0xD0, 0xCA, 0x17, 0x53, 0xB1, 0x71, 0x51, 0x02, 0x12, 0x8E, 0x12, 0xC9, 0x1A, 0x17, 0xA1, 0x29, 0xCA, 0xDD, 0xB6, 0x7A, 0x7B, 0x50, 0x90, 0x4C, 0xE8, 0xDE, 0x82, 0x85, 0xF2, 0xC9, 0x23, 0xAC, 0x38, 0x14, 0x95, 0xD6, 0x43, 0x4A, 0x6A, 0x66, 0x5E, 0x94, 0xE8, 0xE3, 0xAC, 0x5D, 0xCB, 0x4F, 0x94, 0x49, 0x5E, 0x99, 0xD7, 0x44, 0x51, 0x3E, 0x30, 0xD0, 0xB9, 0xDD, 0x9C, 0x8D, 0x72, 0x92, 0x08, 0xC4, 0x2C, 0x0B, 0xDF, 0xDA, 0x4D, 0x4F, 0x00, 0x0A, 0xF4, 0x92, 0x9C, 0x87, 0x86, 0x00, 0x94, 0x43, 0xAA, 0x0B, 0x4B, 0x69, 0x57, 0xE3, 0x1D, 0x63, 0xA3, 0x71, 0x81, 0xE4, 0x25, 0x71, 0x15, 0xA7, 0x8F, 0x7A, 0x5E]
rdk=[0x0C, 0x38, 0x93, 0x17, 0x54, 0xF7, 0xA7, 0x11, 0x20, 0xC8, 0x89, 0xF7, 0x25, 0xFA, 0x1A, 0xD4, 0x50, 0x13, 0xAA, 0xA0, 0x04, 0xE4, 0x0D, 0xB1, 0x24, 0x2C, 0x84, 0x46, 0x01, 0xD6, 0x9E, 0x92, 0x0B, 0x7B, 0x48, 0xBD, 0x0F, 0x9F, 0x45, 0x0C, 0x2B, 0xB3, 0xC1, 0x4A, 0x2A, 0x65, 0x5F, 0xD8, 0x7E, 0x8A, 0x11, 0x62, 0x71, 0x15, 0x54, 0x6E, 0x5A, 0xA6, 0x95, 0x24, 0x70, 0xC3, 0xCA, 0xFC, 0xDA, 0xCF, 0x2B, 0x0A, 0xAB, 0xDA, 0x7F, 0x64, 0xF1, 0x7C, 0xEA, 0x40, 0x81, 0xBF, 0x20, 0xBC, 0xAB, 0xD7, 0x37, 0xB9, 0x00, 0x0D, 0x48, 0xDD, 0xF1, 0x71, 0xA2, 0x9D, 0x70, 0xCE, 0x82, 0x21, 0x42, 0x92, 0xA8, 0x9E, 0x42, 0x9F, 0xE0, 0x43, 0xB3, 0xEE, 0x42, 0xDE, 0xC3, 0x20, 0xC0, 0xFF, 0x40, 0xA8, 0x0B, 0x70, 0x02, 0x37, 0xEB, 0x33, 0xB1, 0xD9, 0xA9, 0xED, 0x72, 0xF9, 0x69, 0x12, 0x9D, 0xFC, 0x86, 0x1D, 0x9F, 0xCB, 0x6D, 0x2E, 0x2E, 0x12, 0xC4, 0xC3, 0x5C, 0xEB, 0xAD, 0xD1, 0xB7, 0xA2, 0x7B, 0x87, 0x28, 0x69, 0x16, 0xA9, 0x06, 0x7B, 0xD2, 0x6A, 0x5A, 0x90, 0x7F, 0xBB, 0x49, 0x08, 0x0F, 0x77, 0x61, 0x61, 0x19, 0xDE, 0x67, 0x1A, 0xCB, 0xB4, 0x3D, 0x8A, 0xB4, 0x0F]
enc=[0x0000004E, 0x00000054, 0x000000D6, 0x00000026, 0x000000C7, 0x00000097, 0x00000097, 0x0000008B, 0x00000006, 0x000000E5, 0x00000009, 0x0000009E, 0x000000BE, 0x00000057, 0x00000008, 0x0000004E, 0x00000028, 0x0000002A, 0x0000008A, 0x0000007F, 0x00000088, 0x000000C9, 0x000000F7, 0x000000EB, 0x000000E2, 0x000000BA, 0x000000F4, 0x0000005E, 0x000000E1, 0x00000040, 0x000000C0, 0x0000005A]
rdk2=[0x2A, 0xEE, 0xC7, 0x59, 0xDF, 0x60, 0x30, 0xD6, 0xBE, 0xC1, 0x6C, 0xF1, 0x6B, 0xF2, 0x4D, 0x6A, 0x3C, 0x85, 0x5A, 0xAF, 0xE3, 0xE5, 0x6A, 0x79, 0x5D, 0x24, 0x06, 0x88, 0x36, 0xD6, 0x4B, 0xE2, 0xB0, 0x94, 0xB8, 0x0A, 0x53, 0x71, 0xD2, 0x73, 0x0E, 0x55, 0xD4, 0xFB, 0x38, 0x83, 0x9F, 0x19, 0x70, 0x87, 0x40, 0xC1, 0x23, 0xF6, 0x92, 0xB2, 0x2D, 0xA3, 0x46, 0x49, 0x15, 0x20, 0xD9, 0x50, 0x37, 0xCA, 0xE3, 0xE8, 0x14, 0x3C, 0x71, 0x5A, 0x39, 0x9F, 0x37, 0x13, 0x2C, 0xBF, 0xEE, 0x43, 0x39, 0xAF, 0xFF, 0xC4, 0x2D, 0x93, 0x8E, 0x9E, 0x14, 0x0C, 0xB9, 0x8D, 0x38, 0xB3, 0x57, 0xCE, 0xA6, 0xBC, 0x86, 0xAB, 0x8B, 0x2F, 0x08, 0x35, 0x9F, 0x23, 0xB1, 0xB8, 0xA7, 0x90, 0xE6, 0x76, 0x8A, 0xF4, 0xF2, 0x71, 0x01, 0xDB, 0xFA, 0x44, 0x9E, 0xF8, 0x4B, 0xFC, 0x39, 0x68, 0xAD, 0x8A, 0xE0, 0xF2, 0xA3, 0x70, 0xE1, 0x29, 0x59, 0x34, 0x7F, 0xD1, 0x12, 0xC8, 0x46, 0xB9, 0xBF, 0x42, 0xD8, 0xBC, 0xE1, 0x77, 0x39, 0x95, 0xB8, 0x43, 0x46, 0x44, 0xAA, 0x8B, 0x00, 0xFD, 0x15, 0xC9, 0x11, 0xCB, 0xA1, 0x0C, 0x28, 0x5E, 0x19, 0x4F, 0x6E, 0x1A, 0xB3, 0xC4, 0x6E, 0xE7, 0xA6, 0x0D]
p1=enc[:16]
p2=enc[16:]
m1=decry(p1,rdk)
print(bytes(m1))
s='jRphhACRh8TquLAKaaaaaaaaaaaaaaaa'
m2=decry(p2,rdk2)
print(bytes(m2))
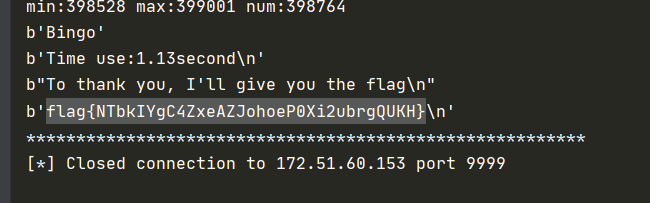
print('flag{jRphhACRh8TquLAKHJuppYiK0gaC4MME}')
|